Keyprints
Keyprints is part of a larger exploration of behavioural keyboard biometrics.
It aims to explain the concept of keystroke patterns and how they are used as unique identifiers of individuals.
Further below, find information on why all that matters.
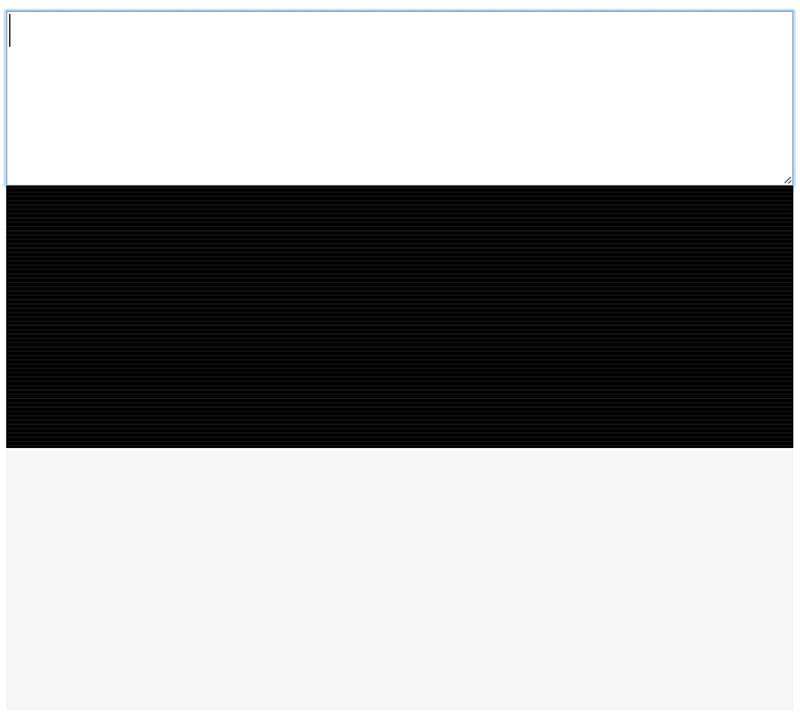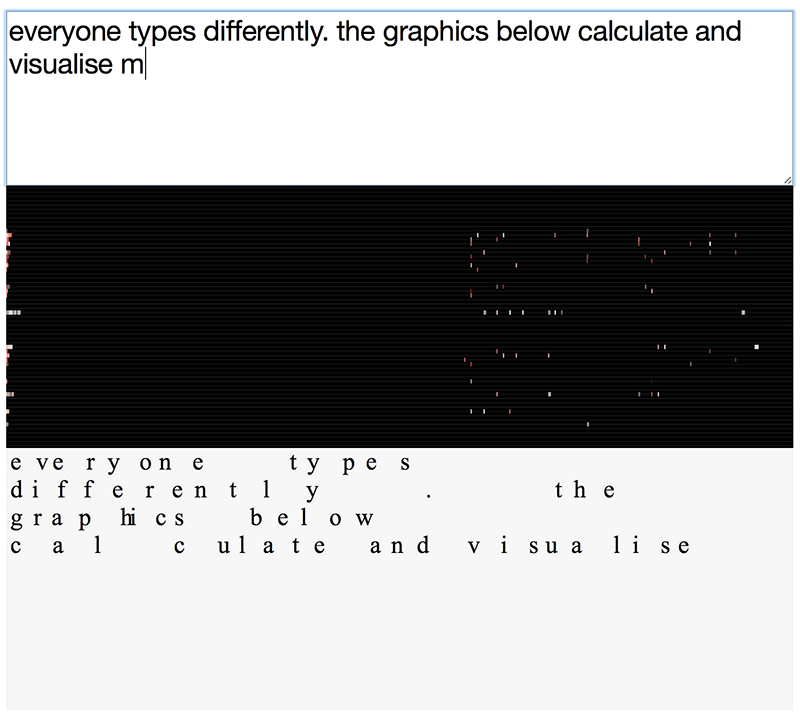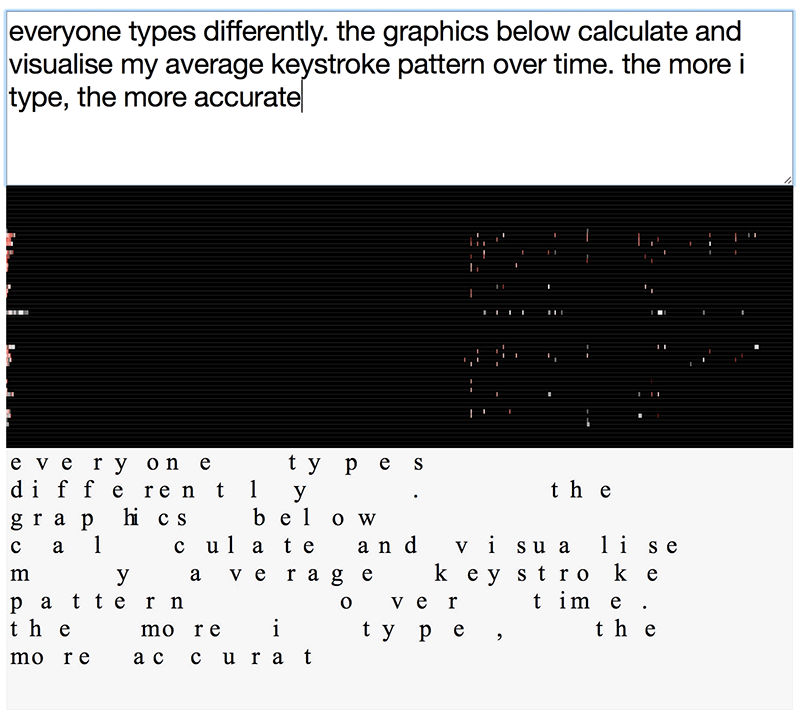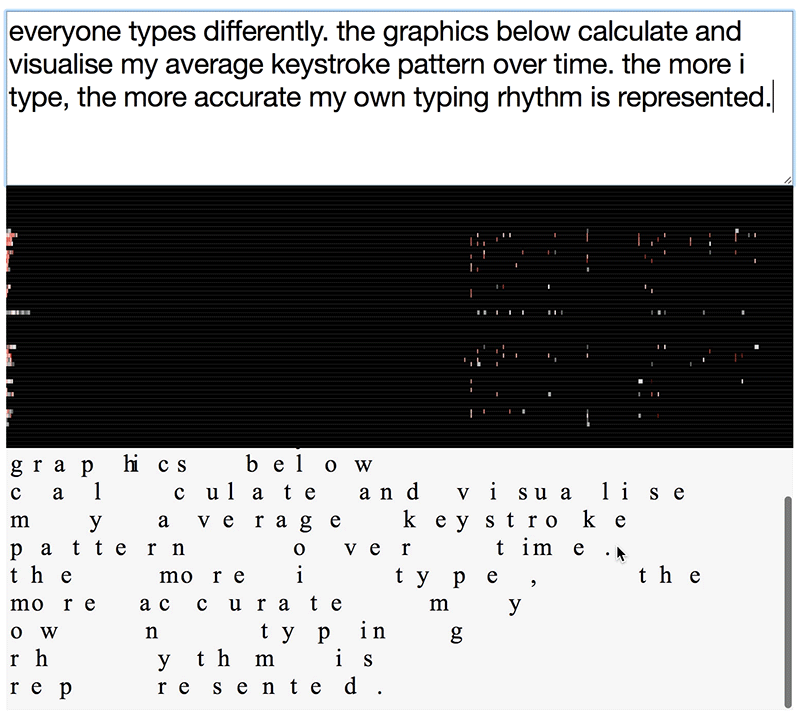
keyprints visualisation of differences in typing patterns
Test the demo yourself at keyprints.leoneckert.com.

keyprint viz of a larger dataset of keystrokes
Why all that matters
The visualisations above will look different for each one of us, even when writing the same text. This is because we all type in slightly different rhythms.
Data sets describing our unique keystroke patterns are of high interest to data collectors (like companies or governments) because they can be used for various things:
Identifying us online - you can visit one website and type something and later go to another one and type something else, the pattern of your keystrokes will match. It does not matter which browser or computer you are using (we do type different on different keyboards, but sophisticated data sets should be able to deal with this fact and still identify not only you, but also the exact (computer/)keyboard you are using). This is more effective than cookies as a means to track us, because it can distinguish between different users of the same device and vice versa. I did an experiment on keystroke identification using python (link coming soon).
Authentication - as stated in Darpa's Active Authentication Program, the use of conventional passwords is "inherently unnatural" and insecure. We (will) authenticate ourselves more and more through software based biometrics defined as unique characteristics of our human computer interaction. Benefits are that we don't have to remember passwords and (,as Darpa states,) that our authentication is "accurate, robust, and transparent".
This is highly debatable. Biometric authentication mehtods like our fingerprint (iPhone), or facial features (airport security) or keystroke and mouse patterns (behaviosec) are already in use. We have to be cautious and sceptical when it comes to giving away data that is not only privat, but more also serves as a way to identify us uniquely and track our behaviour.
Data collection is simple and normally takes place without our awareness. Equally, recreating and spoofing someone else's typing pattern programmatically is not a difficult task either. I did an experiment in python using selenium (link coming soon). If someone is hacking your mail or bank account today, you will most likely be changing your password. However, if someone gets access to an account which you log into using biometric/behavioural authentication methods, changing the 'password' will not be an option anymore as that would entail changing your self.
FAQ
Sounds scary, is this already happening?
Yes, using typing pattern as a means of authentication is already in use. I assume it's also used to track, but I am currently unaware of any concrete examples (contact me if you hear of anything).
How accurate is it?
I currently can't measure the exact level of accuracy however i'd loosely compare it to that of a finger print in the real world.
What can we do against it?
I worked on a proposal called Deceit Board. However this will not save your privacy once and for all. As technology progresses, there is never one definite protection from surveillance that can not be broken soon. Above that, obviously, behavioural keyboard typing surveillance is just a tiny piece of the bigger picture. Not accepting the collection of our data is the most important thing.
Did someone do something similar (to the Deceit Board) before?
Yes, there is a Chrome plugin. The reason I decided to make a physical device is that inside our computer there is little a data collector could not somehow get hold of. The idea was to create a protection device that anonymises data before it reaches your computer altogether.
Any more references?
I read this article the other day.